# Factory Proxy
To automate ABB Ability™ PKI workflow, there is a design consideration to have two main components: Factory Proxy and Certificate Manager Service. This document details how Factory Proxy communicates with Certificate Manager Service and how factory devices can communicate with Factory Proxy.
The following diagram describes core components of Factory Proxy Stack.
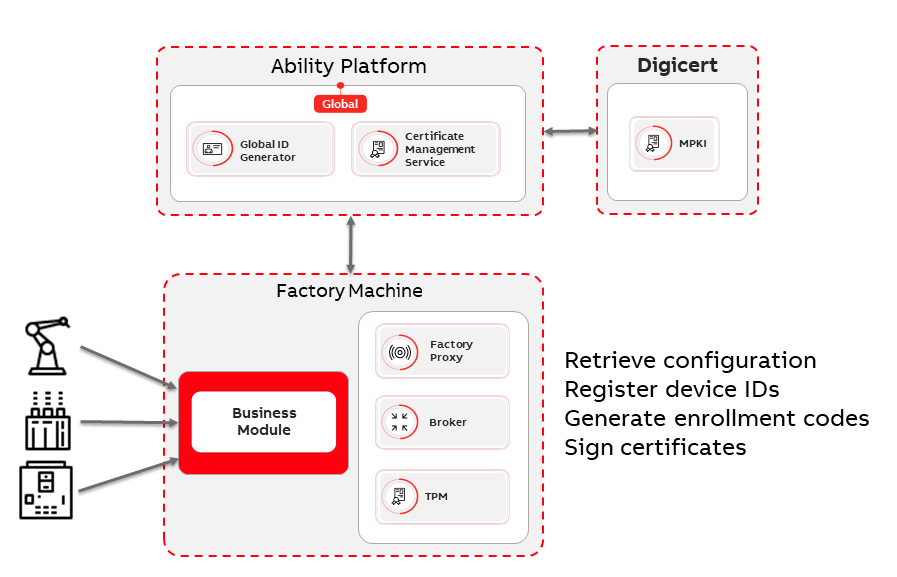
# Factory Proxy and Factory Broker
Factory proxy is installed on a local machine with access to the internet (accessible CM service).
Proxy in general is a communication layer between BU Modules and CM Service to process messages from the message broker into CM and back. It should be built as a Docker image.
MQTT is chosen as the message broker and the modules built by the business units connect to the MQTT bus to send and receive images.
The Factory machine design is very similar to Ability Edge Design and share the following common principles:
- Factory proxy credentials are protected (Application ID and Client Secret) using TPM. The Factory proxy must have access to the credentials whenever it needs those credentials.
- MQTT Broker in a docker environment provides a common messaging framework for communication between the Factory Business modules and Factory Proxy.
- The Factory Proxy performs outbound communication with Azure AD (For authentication of the proxy) and then with CM Service for the factory automation.
- Supports whitelisted outbound communication from custom modules. To ensure compliance to ABB MCSR, this requires additional cyber security controls as documented below:
- In cases where internet connectivity is required for the business modules, configuration allows to split into 2 services:
- Internet facing BL Service (Internet-BL Module)
- Factory Network facing BL Service (Factory-BL Module)
- The Edge docker environment contains two isolated networks
- factory-internet which allows access to Internet facing NIC
- factory-intranet which allows access to Factory internal network.
- The Broker has access to both the networks and resources within them and acts as an authenticated bridge between the two
- Factory proxy resides in factory-internet network
- In cases where internet connectivity is required for the business modules, configuration allows to split into 2 services:
- Factory proxy downloads the configuration and the docker images of the configured BL Modules.
- If a BL module is associated with internet access, then Factory proxy configures the BL module in the factory-internet network
- If no internet association is present, factory proxy configures the BL module in factory-intranet network
Diagram describes Factory Proxy network overview:
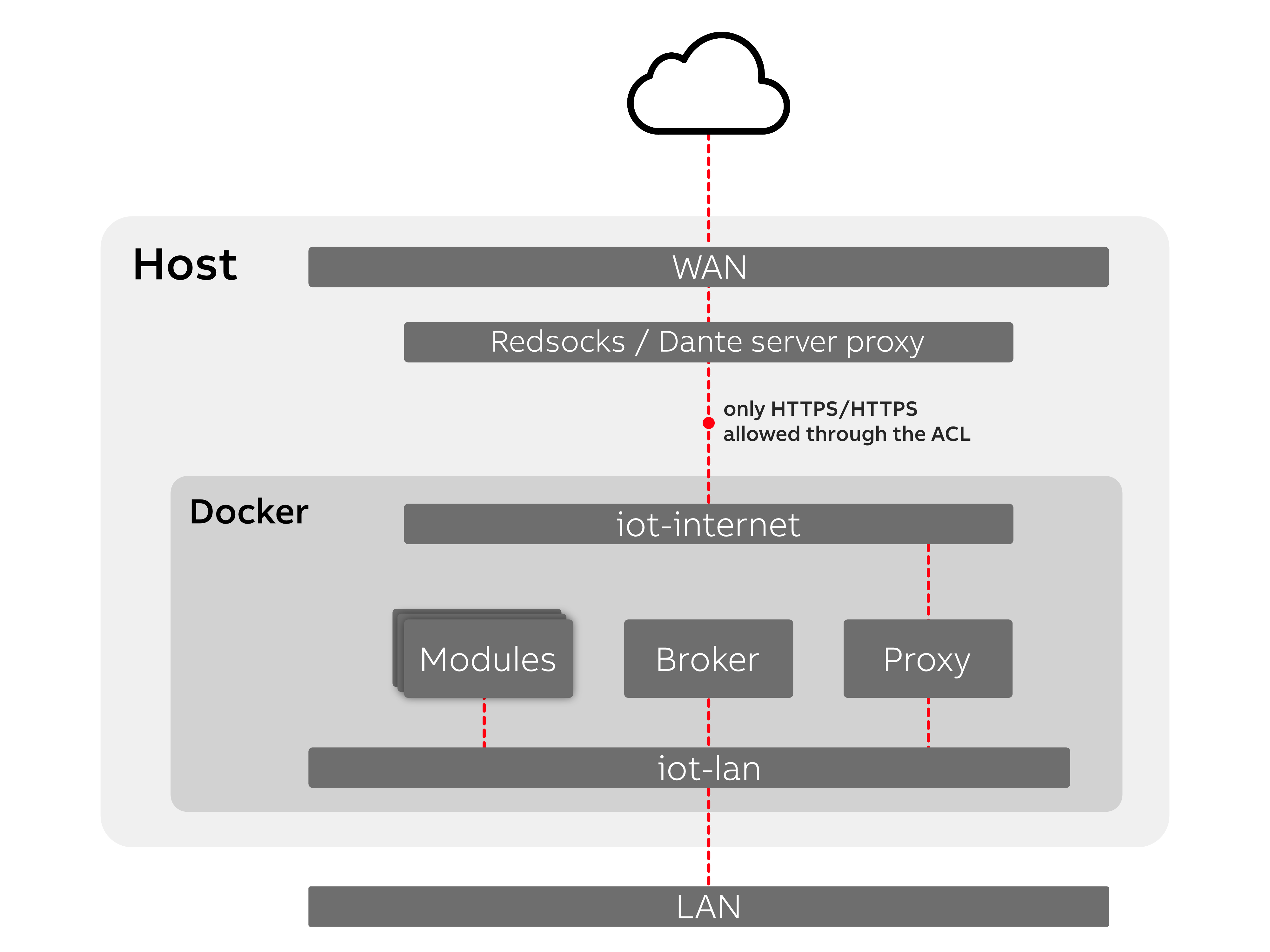
# IP Table Rules Configuration
- Allow established connections to communicate freely
- Permit unrestricted communication from localhost and Docker software networks
- Permit unrestricted communication from specialized software networks (iot-lan, iot-internet)
- Communication within the host itself is unrestricted
# Supported Scenarios
# Online Certificate Enrollment
Factory Proxy can support online enrollment for production line devices capable of sending certificate operations to RA PKI endpoint directly. Please, refer to more detailed process here. In this scenario Factory Proxy module is supposed to order enrollment code and device identifier pairs and deliver them to line's devices:
- Once Factory Proxy is provisioned and ready for production
- Module sends enrollment code generation
- Module awaits code and device Id pairs (delivered only when CM Operation status is changed from pending to new or redeemed or error)
- Module delivers enrollment code and device Id to devices using Factory Intranet
- Device can request Certificate enrollment by using SCEP protocol and provided credentials
# Offline Certificate Enrollment
General concept is described under Offline and it is dedicated for devices not capable of handling operations with RA PKI endpoint. The diagram explains the setup:
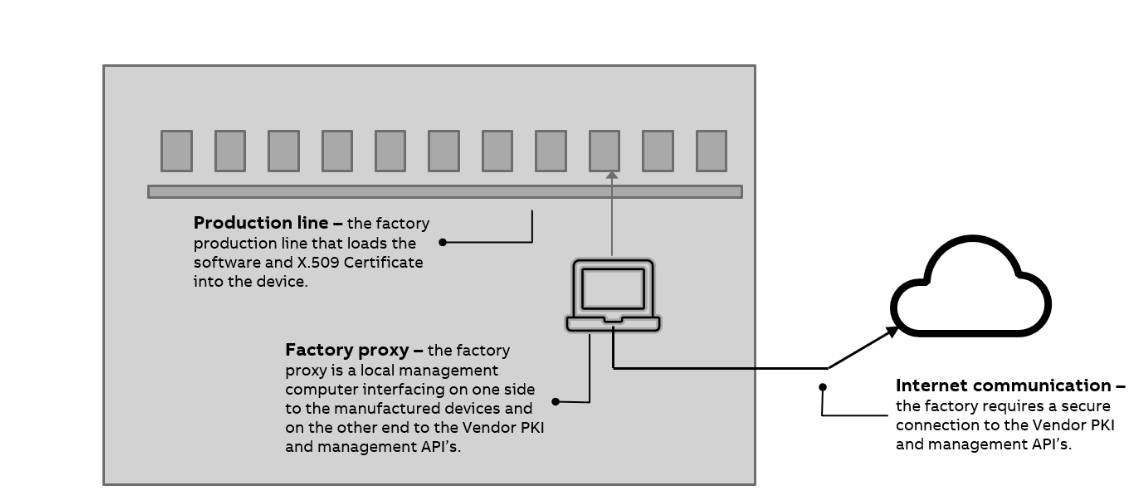
Key differences to online scenario are:
- Line device is not allowed or capable of sending PKI request i.e.: via SCEP
- Line device is still supposed to generate and protect private key
- Certificate delivery looks as follows:
- Factory Proxy Module Generates Enrollment Codes and Device Ids
- Factory Proxy Module delivers Device Id
- Line device generates CSR based on Device Id and sends it to Proxy Module
- Factory Proxy Module enroll and deliver device certificate
# Module Development
Please refer to Factory Proxy API
