# Custom Container Registry
This article will explain how to configure Factory Proxy to use your own container registry instead of the default abbability.azurecr.io one.
abbability.azurecr.io registry
You can use the abbability.azurecr.io registry during the DEVELOPMENT phase of your project. For the PRODUCTION phase, you will want to have your own registry fully controlled by you.
# Setting up your own registry
First of all, you need to have your own registry up and running. It needs to be accessible to:
- the Factory Proxy machine
- the persona that deploys the module images there
One possibility of setting this up is with the usage of Azure Container Registry. To create it, follow the steps outlined on MSDN. Make sure that you configure the access to this registry according to your business requirements.
When your registry is up and running, push your module image(s) there. Here's an example:
# Build your docker image
docker build -t <REGISTRY>/<IMAGE>:<TAG>
# Login to your docker registry
docker login <REGISTRY>
# Push the image
docker push <REGISTRY>/<IMAGE>:<TAG>
Additionally, push the system modules as well (the versions/tags are just an example. We recommend to use the latest released versions of the system modules):
# Copy the factory-proxy system module
docker pull abbability.azurecr.io/factory.machine/factory.proxy:1.0.1
docker tag abbability.azurecr.io/factory.machine/factory.proxy:1.0.1 <REGISTRY>/factory.proxy:1.0.1
docker push <REGISTRY>/factory.proxy:1.0.1
# Copy the factory-broker system module
docker pull abbability.azurecr.io/factory.machine/factory.broker:1.0.0
docker tag abbability.azurecr.io/factory.machine/factory.broker:1.0.0 <REGISTRY>/factory.broker:1.0.0
docker push <REGISTRY>/factory.broker:1.0.0
In the example above the folowing values need to be defined by you:
<REGISTRY>- the URL of your container registry<IMAGE>- the name of your module's image<TAG>- the tag of your image
# Configuring Factory Proxy
To use your private registry as a source of images on the Factory Proxy machine, you need to apply proper configuration in the Certificate Manager Portal (or through the API if you prefer to do so), and on the machine itself.
# Certificate Manager
Go to your Factory Proxy instance in the Factory proxies tab (or create a new instance if you do not have one yet). Follow the typical setup as outlined in the Onboarding article, with a few remarks below.
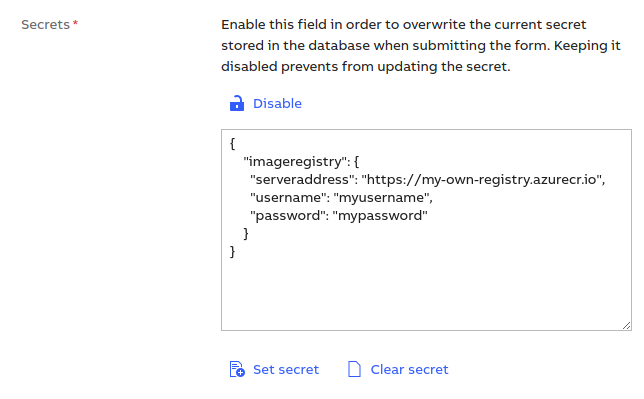
# Secrets
You need to configure the Secrets of your Factory Proxy (still in the Certificate Manager Portal) - provide the address and the credentials of your custom containe registry. Here's an example:
# Configuration
Then, in the Configuration section of your Factory Proxy instance, among others, you need to provide the URLs of all of the modules. Make sure that the URLs point to the right registry. You can see an example of how the configuration looks like in the Onboarding article.
# Factory Proxy Machine
If you look at the Installation procedure,
one of the steps is to edit the /var/ability/factoryproxy/factoryproxy.env
file. By default, it is configured with the abbability.azurecr.io container
registry. You can replace that default with the address of your own registry
instead:
IMAGEREGISTRIES={"abb":{"serveraddress":"https://<CUSTOM_REGISTRY_ADDRESS>"}}
Make sure that you provide the same address as in the Certificate Manager Portal
(i.e.,
IMAGEREGISTRIES={"abb":{"serveraddress":"https://my-own-registry.azurecr.io"}}).
# Installation
When you start the Installation process, you will be asked to provide (among others) the credentials of your container registry (username and password). Make sure that you provide the same credentials as you did in the Secrets section of your Factory Proxy setup in the Certificate Manager Portal. This step is necessary for the machine to be able to login and pull the factory-proxy system module for the first time from the registry. Only when factory-proxy module is up and running, it will be able to communicate with the Certificate Manager Service to read your configuration and secrets from there.
